The latest Annual Cyber Threat Report from the Australian Signals Directorate (ASD) confirms what many in the market have been feeling for some time: financial and insurance services are now one of the most attractive targets for cyber attackers in Australia.
In 2024–25, ASD’s Australian Cyber Security Centre (ACSC) received over 84,700 cybercrime reports – about one every six minutes. The average self-reported loss per business incident jumped to $80,850, a 50% increase in a single year. For small firms the average hit was $56,600; for medium enterprises, $97,200; and for large organisations, $202,700. cyber.gov.au
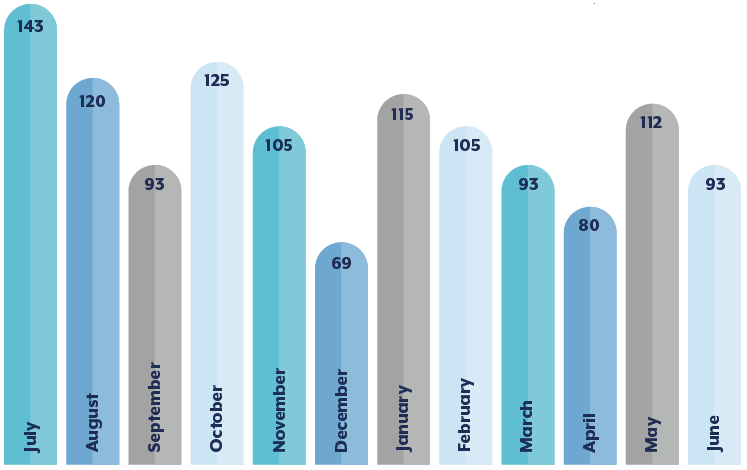
Figure 1: Cyber security incidents responded to by month
For an industry built on managing risk, these are not abstract numbers. They describe a structural shift in exposure for insurers, brokers and their customers.
ASD’s data shows that when Australian organisations report cyber incidents, financial and insurance services now account for around 7% of all cases – the highest share of any non-government sector. cyber.gov.au
Only the federal and state/local public sectors generate more incident reports. In other words, insurers now sit alongside government as front-line targets.
Two data points stand out:
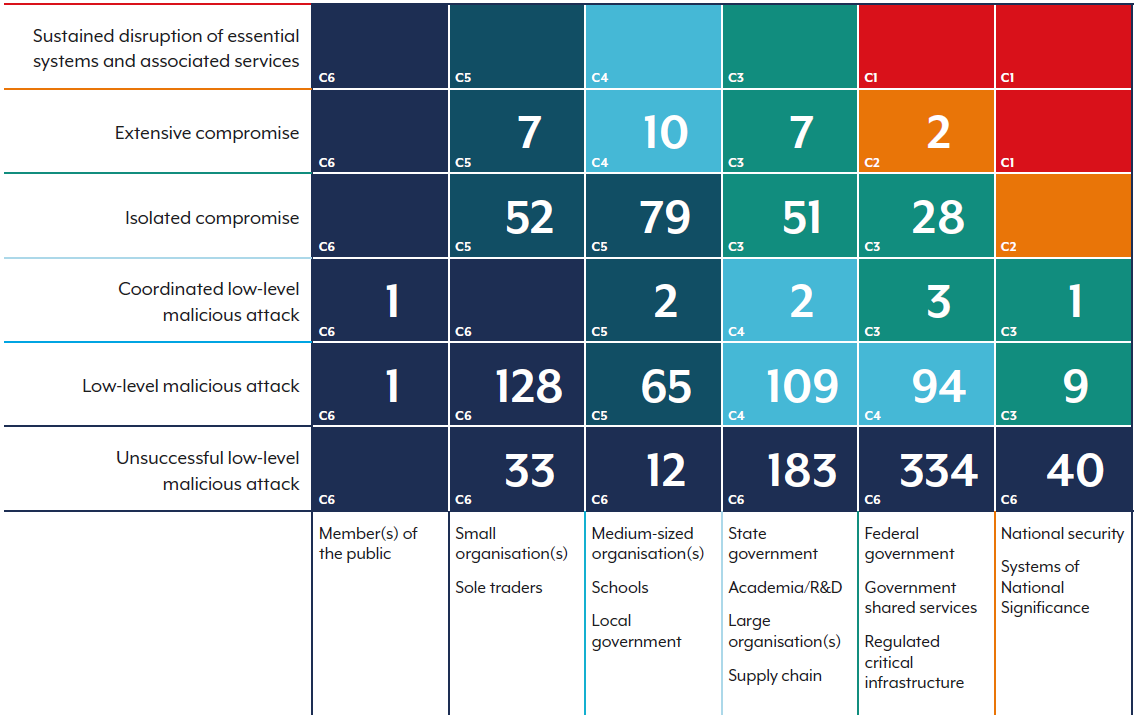
Figure 2: Cyber security incidents by severity category for FY2024–25 (total 1,253)
For boards and executives, this is the crux: insurers aren’t just another commercial target; they’re treated as critical to national economic stability. That raises the stakes for operational resilience, regulatory expectations and incident response capability.
The stereotype of a cyber attack as “a virus in an email” is now badly out of date.
ASD highlights a continuing “campaign of credential theft”, with criminals buying stolen usernames and passwords on the dark web and using them to access email, social media and financial accounts. Identity fraud remains the top-reported cybercrime type nationally.
Figure 3: Example of an info stealer ecosystem and possible impact on an organisation
CrowdStrike’s 2025 Global Threat Report paints a similar picture globally:
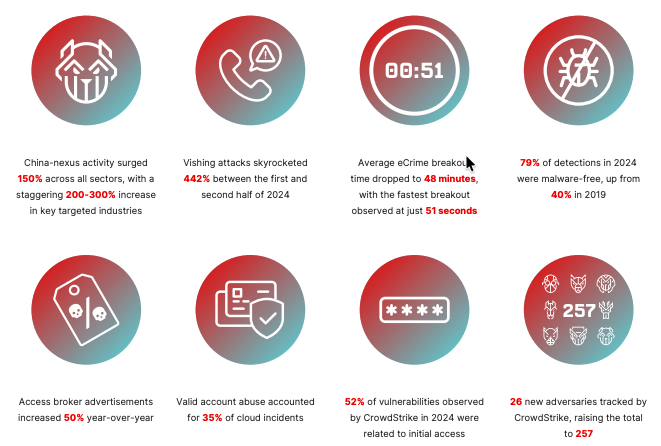
For insurers, three themes matter most:
The direction is clear: attackers are behaving like professional enterprises, moving fast, reusing playbooks that work, and focusing on identity and availability rather than just dropping ransomware and hoping for the best.
Figure 4: Prevalence of top 10 MITRE ATT&CK techniques in FY2024–25
ASD’s executive summary is blunt: businesses should “operate with a mindset of ‘assume compromise’” and identify the “crown jewels” that must be protected first. cyber.gov.au
To get there, ASD recommends four “big moves” for organisations:
ASD also stresses the basics: strong multi-factor authentication, unique passwords or passphrases, timely patching, phishing awareness and regular backups. These alone could prevent the majority of incidents reported to the agency. cyber.gov.au
Given the sector’s prominence in both incident statistics and critical infrastructure reporting, insurers can expect continued attention from regulators, customers and government on cyber resilience. cyber.gov.au
That means:
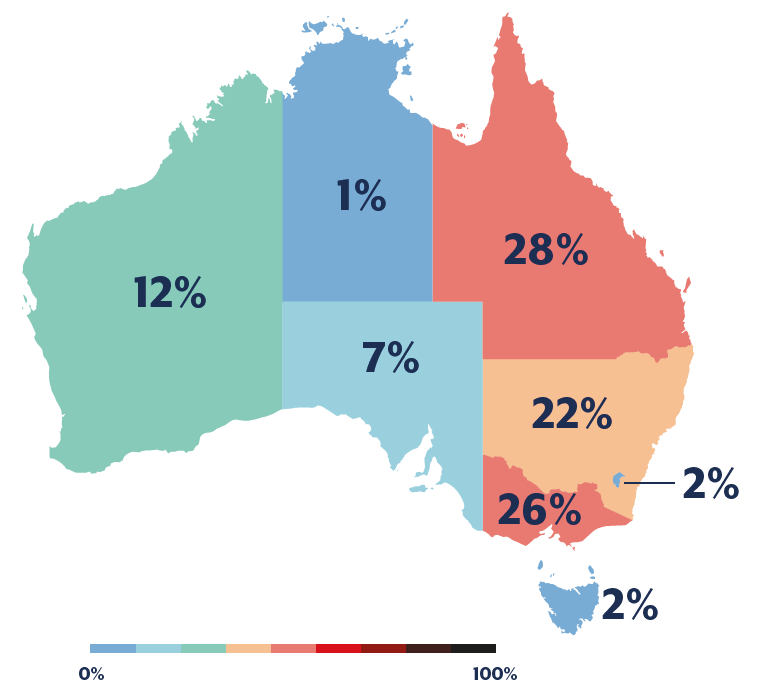
Figure 5: Breakdown of cybercrime reports by jurisdiction for FY2024–25
With the average business incident now costing $80,850 – and considerably more for medium and large enterprises – cyber loss is a board-level financial exposure, not just an IT problem.
For cyber and professional lines underwriters, this fuels:
Pricing, coverage wording and risk selection will need to reflect that attacks are faster, more targeted and more identity-driven than even a few years ago.
Brokers and MGAs increasingly rely on digital portals, embedded insurance and real-time data flows. These same channels are attractive targets for attackers seeking:
Resilience of these shared platforms becomes a core part of the client value proposition, not just a back-office concern.
InsuredHQ operates in the middle of these shifts – as a technology provider to insurers, brokers and MGAs, and as a custodian of sensitive policyholder and financial data.
Without turning this into a product pitch, there are a few concrete ways platforms like InsuredHQ can and should support the response ASD is calling for:
InsuredHQ’s role is not to replace an organisation’s cyber security stack, but to provide a secure, well-instrumented backbone for revenue-critical insurance operations – one that supports, rather than undermines, the controls your security and risk teams are trying to enforce.
ASD’s latest report and global threat intelligence tell the same story:
For insurers and intermediaries, cyber risk is now inseparable from business risk. The immediate priority is not simply “buy more security tools”, but to:
Ignoring this isn’t just a technology decision anymore. It’s a strategic one.
These Stories on insurance
Copyright © 2023 InsuredHQ Limited. All Rights Reserved - InsuredHQ Privacy Policies - Glossary
No Comments Yet
Let us know what you think